Key facts
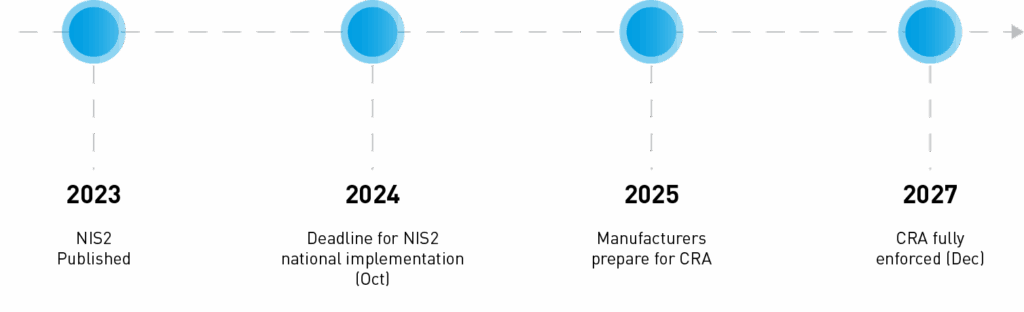
EU manufacturers are facing a double challenge when it comes to cybersecurity. From October 2024, the NIS2 Directive will require companies in critical sectors—like manufacturing—to follow strict rules around cyber risk management, incident response, and supply chain security. Then, from December 2027, the Cyber Resilience Act (CRA) will kick in, mandating that all digital products placed on the EU market meet robust security standards by design.
Together, these laws mark a major shift in how cybersecurity is regulated in the EU. Manufacturers must now treat digital risk as seriously as physical safety.
Key points at a glance:
- NIS2 applies to organisations in key sectors, including manufacturing.
- CRA applies to any product with digital elements sold in the EU.
- NIS2 requires 24-hour incident reporting and risk-based controls.
- CRA demands secure product design and 5 years of security support.
- Non-compliance could lead to fines up to €15 million.
This article breaks down what both laws mean for manufacturers using industrial software—and how to prepare before the deadlines arrive.
Table of Contents
- Key facts
- Complying with the EU Cyber Resilience Act and NIS2: A Guide for Industrial Manufacturers
- What Are the CRA and NIS2?
- Obligations for Manufacturers Under the Cyber Resilience Act (CRA)
- Obligations for Manufacturers Under NIS2
- Key Cybersecurity and Risk Management Practices for Compliance
- Software Supply Chain Security Considerations
- How CRA and NIS2 Build on the Existing Regulatory Landscape
- Conclusion: Turning Compliance into Opportunity
Complying with the EU Cyber Resilience Act and NIS2: A Guide for Industrial Manufacturers
As manufacturing operations become more digitised and connected, European regulators have introduced two landmark measures to strengthen cybersecurity: the Cyber Resilience Act (CRA) and the revised NIS2 Directive. These new rules aim to protect both the products manufacturers make and the industrial systems they use. For manufacturers running industrial software (such as Rockwell Automation’s platforms), understanding and complying with CRA and NIS2 is now a critical priority. This guide explains the purpose and scope of each law, the obligations they impose, and how manufacturing firms can meet these requirements through sound cybersecurity and risk management practices.
What Are the CRA and NIS2?
Cyber Resilience Act (CRA): The CRA is a European Union regulation focused on the cybersecurity of products with digital elements. It introduces mandatory security requirements that manufacturers must build into hardware and software before those products can be sold in the EU. In essence, the CRA adds a cybersecurity dimension to the familiar CE marking regime for product safety. From 2027 onward, any “product with digital elements” (essentially, any device or software that can connect to another device or network) will need to meet baseline security standards or it cannot be offered on the EU market. The CRA emphasises secure-by-design development, ongoing vulnerability management, and transparent security information throughout a product’s lifecycle. Being an EU regulation (not a directive), it applies directly across all member states after a transition period – with main obligations kicking in by December 2027.
NIS2 Directive: NIS2 is the EU’s Second Network and Information Security Directive, which updates and strengthens the original 2016 NIS directive. Its focus is on improving cybersecurity practices at the organisational level for operators of essential and important services across critical sectors. NIS2 significantly broadens the range of sectors covered – including manufacturing, chemicals, waste management, food, and more – beyond the traditionally recognised critical infrastructures like energy, transport, water, health, and digital infrastructure. By October 2024, EU countries must transpose NIS2 into national law. Companies classified as “essential” or “important” entities under those laws will then have binding obligations to implement cybersecurity risk management measures and report cyber incidents. NIS2 essentially sets a higher baseline of cyber hygiene and governance, with the aim of reducing breaches and improving resilience in vital supply chains.
Under NIS2, a wide range of sectors are covered. “Essential entities” (examples in green) include traditional critical infrastructures like energy, transport, health, and finance, whereas many manufacturing and industrial sectors (examples in grey) are designated as “important entities.” Both categories must comply with NIS2’s security requirements, though important entities may face slightly lower penalty thresholds.
Why two separate laws? In brief, NIS2 addresses organisational and operational security (ensuring that companies in key sectors practice good cybersecurity and incident response), while the CRA addresses product security (ensuring that any digital product placed on the EU market is cyber secure by design). They are complementary. A manufacturing firm may be covered by NIS2 as an “important entity” required to manage cyber risks in its factories, and it may also need to comply with the CRA if it produces or integrates digital products (like smart machines or industrial control software) for the market.. Together, these initiatives create a more consistent and comprehensive cybersecurity framework across Europe.
Obligations for Manufacturers Under the Cyber Resilience Act (CRA)
The Cyber Resilience Act places direct obligations on manufacturers of products with digital elements to ensure those products are secure before and after they reach customers. Key duties under the CRA include:
- Secure Product Design and Development: Manufacturers must design and build products following “security-by-design and by-default” principles. Security risks should be considered from the outset of development. For example, products should include necessary access controls, encryption for data, and protections against unauthorised access as default settings.
- Essential Security Requirements: The CRA defines a set of essential cybersecurity requirements (listed in Annex I of the Act) that every in-scope product must meet. These cover both protections during design and security during operation of the product. In practice, this means conducting thorough risk assessments of the product and implementing measures to mitigate identified risks. Even though the law’s text is high-level, detailed harmonised EU standards are being developed to guide what technical controls and processes are needed for compliance.For industrial software or devices, manufacturers will likely draw on standards like IEC 62443 (industrial control system security) or ISO 27001 to help meet these requirements.
- Technical Documentation and Security Information: For each product, manufacturers must prepare comprehensive technical documentation demonstrating how it meets the CRA’s essential requirements. This documentation must include things like the product’s architecture and design details, the risk analysis performed, and the vulnerability management processes in place (including a Software Bill of Materials, or SBOM).. Additionally, manufacturers have to provide clear user instructions and security information with the product. These should tell customers how to use the product securely – for instance, configuration steps at installation, how to apply security updates, and warnings about insecure usage practices. In effect, the user should receive a sort of “cybersecurity handbook” for the product as part of its documentation.
- Conformity Assessment and CE Marking: Before a product can be sold in the EU, the manufacturer must carry out a conformity assessment to verify the product meets the CRA’s requirements. For most products, this can be a self-assessment where the manufacturer internally verifies compliance (and assumes responsibility). However, for certain higher-risk categories of products, a third-party notified body must test or audit the product’s security before approval. (These high-risk categories – listed in Annex III/IV of the CRA – include things like industrial control systems, critical network equipment, certain IoT devices, and other sensitive products that could greatly impact security.) Once the appropriate assessment is done, the manufacturer issues an EU Declaration of Conformity and affixes the CE marking to the product as a declaration that it meets all applicable requirements, including cybersecurity. This process mirrors other product regulations: the CE mark now effectively has a cybersecurity component in addition to safety.
- Maintenance and Patching Obligations: Compliance is not a one-off at product launch – the CRA mandates ongoing responsibilities. Manufacturers must provide security updates and support for their products for a reasonable period. In fact, the Act specifies at least 5 years of security support after a product enters the market (or for the expected lifetime of the product if shorter). Security updates released during that support window should remain available to users for at least 10 years after release. This ensures even devices in the field for a long time can be updated against new threats. For manufacturers using industrial software, this means planning for long-term patch availability and not obsoleting support too quickly – a crucial point for factory equipment that may have a decade-plus service life.
- Vulnerability Disclosure and Incident Reporting: A core part of CRA compliance is having a robust vulnerability handling process. Manufacturers must set up a way for security flaws in their products to be reported (e.g. providing a contact point for researchers or customers to disclose vulnerabilities). They are expected to monitor for and address vulnerabilities in any components (including third-party software libraries) in their products. Importantly, if the manufacturer becomes aware of an actively exploited vulnerability in the product or any incident that significantly impacts the product’s security, they have a duty to notify authorities. Under the CRA, manufacturers must report such issues via an EU portal (to be run by ENISA) “without undue delay” – with an initial early warning within 24 hours of detection and a fuller report within 72 hours. For example, if a flaw in an industrial control software is found being used by attackers in the wild, the maker of that software must alert regulators within one day. These reporting obligations push manufacturers to be transparent and swift in handling cyber threats to their products.
Non-compliance with the CRA can lead to stiff penalties, reflecting how seriously the EU views product security. Regulators may impose fines up to €15 million or 2.5% of global annual turnover (whichever is higher) for the most serious infringements. In short, industrial product manufacturers need to treat cybersecurity as a core part of product quality – from initial design through long-term support – to meet the CRA.
Obligations for Manufacturers Under NIS2
If your manufacturing organisation falls under NIS2’s scope as an essential or important entity, you will face a broad set of cybersecurity governance and risk management obligations under the directive. NIS2 is about ensuring companies running critical operations (including many in manufacturing supply chains) adhere to baseline best practices. Key requirements include:
- Implement a Cybersecurity Risk Management Programme: NIS2 requires companies to “implement appropriate and proportionate risk management measures” to address cyber threats. In practice this starts with conducting regular risk analyses of your information systems and industrial control systems. Based on those risk assessments, organisations must have security policies and controls in place to mitigate identified risks. For a manufacturer, this might involve evaluating the risk of a malware outbreak on plant floor networks and then deploying safeguards (like network segmentation or updated antivirus on HMIs) to reduce that risk.
- Baseline Security Measures: Article 21 of NIS2 spells out a minimum set of measures that covered entities must implement. These include:
1) Security policies and procedures based on risk analysis – e.g. documented processes for managing OT system security.
2) Incident handling – having capabilities for detecting, reporting, and responding to incidents. This means establishing an incident response plan for cyber-attacks or breaches, and internal drills to handle ransomware or ICS malware scenarios.
3) Crisis management and business continuity – plans to ensure the business can recover and maintain critical production if a cyber incident causes disruption. For example, a contingency to manually operate certain processes if control systems go down, and regular backups of production data.
4) Supply chain security – measures to assess and secure the supply chain, including cybersecurity due diligence on suppliers and ensuring your vendors (like software providers or equipment OEMs) follow adequate cybersecurity practices. We discuss more on this below.
5) Security of network and information systems – technical measures to secure networks and systems, such as firewalls, intrusion detection, secure configurations, and system monitoring. In an OT setting, this could involve isolating industrial networks from the internet, whitelisting software on control devices, and hardening PLC and SCADA system configurations.
6) Incident response and crisis communication – clearly defined processes to notify affected parties and regulators about incidents. NIS2 imposes strict incident reporting deadlines: regulators must be informed within 24 hours of a significant cyber incident’s detection, with a detailed report within 72 hours and a final assessment within one month. Manufacturers need to be prepared to meet these timelines, which may involve setting up 24/7 monitoring or external cybersecurity partners to detect and report incidents quickly.
7) Cyber hygiene and training – NIS2 recognises that technology alone isn’t enough; organisations must promote good cyber hygiene practices and conduct regular cybersecurity training for staff. For example, factory personnel should be educated on identifying phishing emails or on safe USB device use to prevent introducing malware into industrial control systems.
8) Security of data and encryption – protecting the confidentiality and integrity of data through measures like encryption and secure data storage.
9) Access controls and identity management – improved identification and authentication measures, meaning strong password policies, multi-factor authentication for remote access, and proper user access management on critical systems.
10) Human resources security – policies around personnel, such as background checks for staff in sensitive roles and security awareness requirements.
- Designation of Security Responsible Persons: NIS2 will require organisations to formally designate one or more individuals responsible for compliance and contact with authorities. Companies may have to register with their national regulator and provide a contact point for NIS2 communications. For manufacturing firms operating in multiple EU countries, this can be complex – you might need to register in each country where you have substantial operations, since the “main establishment” principle (one-country registration) may not always apply to distributed manufacturing sites.
- Incident Reporting and Response: As noted, a major change with NIS2 is the tight incident reporting timeline. Any significant cyber incident (one that causes substantial operational disruption or financial loss, or affects other entities) must be notified to the competent authority within 24 hours of detection. Additional updates (a detailed incident report) are typically required within 72 hours, and a final post-incident report within one month. This means manufacturers must have internal processes to rapidly escalate cybersecurity incidents (whether IT or OT) to their incident response team and legal/compliance teams. It’s also wise to have contacts with your national CSIRT (Computer Security Incident Response Team) for guidance. Beyond reporting, effective response is critical – NIS2 pushes firms to handle incidents in a way that minimises impact on the wider supply chain. For example, if a ransomware attack hits a key manufacturing plant, you not only inform regulators, but you may need to alert important downstream customers or partners, especially if you supply other NIS2-regulated industries like healthcare or energy. NIS2 fosters a view that cybersecurity is a shared responsibility across interconnected supply chains.
- Supply Chain Coordination: Relatedly, NIS2 expects greater transparency and cooperation along the supply chain during cyber incidents. Manufacturers deeply embedded in others’ supply chains should anticipate “flow-down” obligations – key customers might incorporate contractual clauses requiring their suppliers to promptly inform them of breaches and to collaborate on incident response. Thus, improving your own incident response capabilities (including communication plans that involve suppliers and customers) is part of NIS2 compliance.
- Oversight and Penalties: NIS2 comes with enforcement teeth. National regulators will supervise compliance, and failure to meet NIS2 obligations can result in fines up to €10 million or 2% of worldwide annual turnover for essential entities (and up to €7 million or 1.4% for important entities). Senior management can be held accountable for non-compliance in some cases. The reputational damage of being publicly called out for a serious cybersecurity lapse is another strong incentive to comply. Overall, cybersecurity is no longer just “best practice” for manufacturers – it is a legal requirement, with real consequences for negligence.
Key Cybersecurity and Risk Management Practices for Compliance
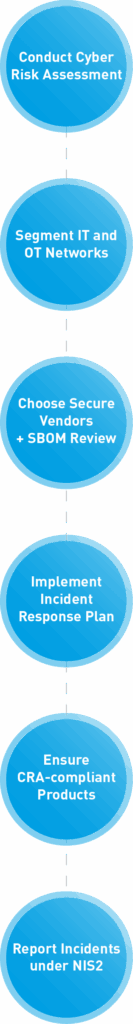
For manufacturers using industrial software and systems, complying with CRA and NIS2 might sound daunting. However, the core practices required are fundamentally aligned with good cybersecurity management that many organisations are already pursuing. Here are key steps and best practices to meet these regulations:
- Adopt a Security Framework: Leveraging established cybersecurity frameworks can provide a roadmap for compliance. Many manufacturers already follow standards like ISO/IEC 27001 (information security management) or the NIST Cybersecurity Framework for their IT/OT systems. These can be “springboards” to meet NIS2 requirements. Similarly, industrial control system standards such as IEC 62443 offer guidance on securing control networks and product development lifecycles. Mapping your existing security controls against NIS2’s measures is a great starting point.. For example, IEC 62443-3-3 covers network segmentation and access control for ICS – directly supporting the NIS2 mandate for secure network and information systems. If you have an ISO 27001-certified ISMS (Information Security Management System), you will have many governance components in place, but be prepared to extend it (NIS2’s controls are more specific and cover broader parts of the organisation than ISO 27001 alone).
- Secure Your OT Infrastructure: Manufacturers should evaluate and bolster the security of operational technology (OT) environments – the industrial control systems, SCADA, and connected devices on the plant floor. This includes steps like: implementing network segmentation between IT and OT to limit attack spread, updating or isolating legacy systems that can’t be easily patched, using firewalls/IPS at control system perimeters, and ensuring strong authentication for remote access to machines. Many OT networks have older equipment not designed with cybersecurity in mind, so compensating controls are important. Investing in modern security monitoring that covers OT (such as anomaly detection tools for industrial networks) can help meet the NIS2 requirement for detecting incidents in real time.
- Regular Risk Assessments and Audits: Both NIS2 and the CRA insist on a risk-based approach. Conduct periodic cybersecurity risk assessments covering both your enterprise IT systems and factory control systems. Identify what the biggest threats are (ransomware, insider misuse, supply chain exploits, etc.), and evaluate the potential business impact (e.g. production downtime, safety hazards, intellectual property theft). Use these assessments to prioritise security improvements. Additionally, consider third-party audits or penetration testing of your networks and products. For high-risk products, CRA may effectively require external testing/certification, so start integrating rigorous security testing into your product development cycle now. For your plant systems, an OT cybersecurity assessment can highlight gaps against best practices or standards – many solution providers (including Rockwell Automation and others) offer services to help with this.
- Secure Development and Maintenance of Software: If you develop software (or hardware with software) as part of your products or processes, adopt secure development life cycle practices. This means integrating threat modeling, secure coding standards, code review, and security testing into your development process. Ensure your engineering teams are trained in cybersecurity. Establish a vulnerability management process to track and address vulnerabilities in your software or firmware (including open-source components you might use) throughout the product’s life. For example, maintain an inventory of third-party libraries in each application (an SBOM) and subscribe to vulnerability alerts for them so you can patch or update components promptly if a new CVE emerges. These practices not only help comply with the CRA’s product-focused rules but also reduce the risk of incidents that would trigger NIS2 reporting.
- Incident Response Planning: Develop and regularly update an incident response plan that covers both IT and OT incidents. This should include clear roles and communication flows for detecting, analysing, containing, and recovering from cyber incidents. Given NIS2’s emphasis on timely reporting, incorporate guidelines in your plan for when and how to notify regulators and possibly customers/suppliers. Conduct simulation exercises or drills (at least annually) to test your team’s readiness, including scenarios like a ransomware attack halting production or a malware infection in a PLC network. The goal is to identify weaknesses in your response (e.g. unclear decision-making authority, or technical blind spots in detection) and improve before a real incident occurs.
- Training and Cyber Awareness: Humans are often the weakest link. Train your employees – not just office staff, but also engineers and operators on the shop floor – in basic cyber hygiene and recognise their role in security. This could involve toolbox talks on phishing awareness, policies on not using personal USB sticks on industrial machines, and encouraging reporting of suspicious activities. Build a culture where safety and security go hand-in-hand, so that following cybersecurity procedures (like access control, software update protocols, etc.) is seen as integral to maintaining a safe and efficient operation.
- Governance and Leadership Involvement: Ensure management is engaged with cybersecurity governance. Under NIS2, leadership must take responsibility, so brief senior executives and boards on the new legal requirements and the organisation’s cyber risk profile. Establish a cross-functional cybersecurity committee if one doesn’t exist – including IT, OT engineers, production managers, and compliance officers – to oversee NIS2 and CRA compliance efforts. Top-level buy-in will help secure necessary budgets and enforce policies across departments. Cyber resilience should be part of the organisation’s strategic objectives, not just an IT issue.
By implementing these practices, manufacturers will not only tick the compliance boxes for CRA and NIS2, but genuinely improve their security posture. A strong cybersecurity foundation will make it much easier to handle the audits, documentation, and proofs required by regulators, and more importantly, it will reduce the likelihood and impact of cyber incidents on the business.
Software Supply Chain Security Considerations
Modern manufacturers rely on complex digital supply chains – from the industrial control software provided by companies like Rockwell Automation, to open-source libraries in custom applications, to cloud services supporting factory operations. Both the CRA and NIS2 put a spotlight on supply chain security, meaning manufacturers must take steps to ensure that third-party software and systems they use (or embed in their products) are trustworthy and secure.
Under NIS2, supply chain security is explicitly one of the required risk management measures. Organisations need to assess the cybersecurity of their key suppliers and service providers. In practice, this could involve conducting vendor security questionnaires or audits, requiring certain certifications or standards from suppliers, and building clauses into contracts that oblige suppliers to maintain strong cybersecurity and report incidents promptly. For example, if you rely on an outside firm for remote support of your equipment, you should ensure they follow strict authentication and network security controls, since their weakness could become your breach.
The Cyber Resilience Act, on the other hand, helps enforce supply chain security from the product angle. It requires manufacturers to account for the security of any third-party components within their products (hence the requirement to maintain an SBOM and vulnerability management process). If you are a machine builder integrating industrial software or controllers from another vendor, you will need to coordinate closely with those suppliers. Make sure your suppliers (like an automation software provider) can furnish you with up-to-date SBOMs listing libraries and dependencies in their software – this will be crucial for your technical documentation and for tracking vulnerabilities. You may also want to verify that your suppliers follow secure development standards or have undergone relevant certifications (for instance, some industrial control vendors might have IEC 62443-4-1 certification for their secure development lifecycle). Using components that are themselves CRA-compliant will lighten your load. In fact, one benefit of the CRA’s market approach is that over time, products available for purchase in the EU should all meet basic cybersecurity criteria, reducing the risk that a vendor’s insecure product becomes your problem.
Coordinated vulnerability disclosure is another important aspect. Manufacturers should establish channels to share information about vulnerabilities with both suppliers and customers. If a vulnerability is found in a component (say, a commonly used PLC firmware), suppliers and asset owners should communicate so that fixes can be applied quickly. The CRA will enforce this from the manufacturer side by mandating vulnerability disclosure programs and timely patch release. Meanwhile, NIS2’s emphasis on cooperation encourages companies to join information-sharing groups or ISACs (Information Sharing and Analysis Centres) for their sector. For example, a manufacturer could participate in an industry cybersecurity exchange to get early warnings about threats in the supply chain (such as tainted software updates or compromised components) and to share learnings from any incidents they experience.
In practical terms, improving supply chain security may involve actions like: keeping an inventory of all software and hardware assets in your facilities (so you know what needs patching when new vulnerabilities emerge), verifying software integrity (using digital signatures and hashes for software updates to prevent tampering), and evaluating new suppliers’ security maturity as part of procurement. Also, consider cyber risk insurance or contractual agreements that cover supply chain incidents, as these can provide resources in case a supplier-related breach occurs.
Ultimately, a chain is only as strong as its weakest link. The dual focus of NIS2 and CRA on supply chain means manufacturers must look beyond their own walls and work with partners to uplift security across the board. By holding suppliers to high standards and being a reliable partner to your customers, you strengthen the resilience of the entire manufacturing ecosystem.
Examples and Best Practices from Industry Leaders
Leading industrial technology providers and forward-thinking manufacturers have already started aligning with these new regulations, offering examples of how to approach compliance:
- Rockwell Automation’s Approach: As a major supplier of industrial software and control systems, Rockwell Automation has been proactive in addressing NIS2 and preparing for the CRA. Rockwell advises manufacturers to leverage existing cybersecurity frameworks (like NIST CSF, IEC 62443, ISO 27001) to accelerate NIS2 compliance. They suggest a staged approach: auditing current security practices, mapping them to NIS2 gaps, then developing a plan and deploying needed technologies and policies. This kind of structured programme helps ensure nothing is missed. Rockwell also highlights that improving OT security now will “fast-track compliance with future regulations such as the EU Cyber Resilience Act”. In other words, if you raise your organisation’s general cybersecurity maturity (for instance, by segmenting networks, enforcing multi-factor authentication, and implementing continuous monitoring in your plants), you will not only meet NIS2 obligations but also be well prepared when CRA product requirements come into force.
- Security-Enhanced Product Development: Some industrial vendors have adopted secure development lifecycle models in line with standards like IEC 62443-4-1 (for product security). For example, a drive manufacturer or PLC supplier might integrate threat modeling and extensive fuzz testing into their product engineering. Manufacturers sourcing such products benefit because those products are more likely to comply with CRA requirements out of the box. When evaluating suppliers, look for signs of this commitment – e.g. vendors publishing cybersecurity guides for their products, offering timely firmware patches, or obtaining EU cybersecurity certification for certain devices. Using reputable, security-conscious suppliers is a practical way to ease compliance burdens on your end.
- Incident Response in Action: The importance of NIS2’s incident handling provisions is illustrated by real-world cases. When Norsk Hydro (a large aluminium manufacturer) suffered a ransomware attack in 2019, it had to switch to manual operations to keep production going, and it famously chose to be transparent about the incident, earning praise for its handling. That kind of preparedness – having offline alternatives and clear communication – is what regulators want to see. More recently, a 2024 cyber attack on a battery manufacturer (Varta) forced multiple plants to shut down. These events underscore why NIS2 now ropes in manufacturers: disruptions in manufacturing can cascade to other critical sectors. As a best practice, companies are updating business continuity plans to address cyber scenarios specifically (e.g. stocking critical spare parts in case digital ordering is down, or having manual fail-safes for key production steps).
- Integrating Product and Operational Security: The intersection of CRA and NIS2 is apparent for manufacturers of high-tech industrial goods. Consider a company that produces smart factory equipment – under CRA, each product model needs secure design and documentation; under NIS2, the company itself needs robust security operations. Some companies are establishing internal “Product Security Teams” alongside traditional IT/OT security teams to handle these distinct but related areas. The product security team focuses on embedding security into the product lifecycle (meeting CRA duties like SBOM, secure coding, product incident response), while the IT/OT security team focuses on enterprise and factory security (meeting NIS2 duties like protecting systems and responding to incidents in operations). They coordinate closely, especially since a vulnerability in a product can blur the line between product compliance and operational risk. This organisational approach can be a best practice – it ensures dedicated attention to product-centric security compliance without neglecting the protection of the company’s own infrastructure.
- Collaboration and External Support: Many manufacturers are turning to external expertise to navigate these changes. Cybersecurity consultants familiar with industrial environments can perform NIS2 readiness assessments or help implement security controls tailored to OT. Similarly, testing labs and certification bodies in Europe are gearing up for CRA conformity assessments. Engaging with these services early (even before the laws fully apply) can give manufacturers a head-start. It’s also wise to follow industry associations or working groups for manufacturing security – they often publish guidelines or host trainings on NIS2/CRA compliance, and they provide a forum to share experiences. By learning from peers and experts, organisations can avoid reinventing the wheel.
How CRA and NIS2 Build on the Existing Regulatory Landscape
It’s worth noting that CRA and NIS2 are not entirely coming out of the blue – they build upon years of evolving security policy in the EU and beyond. Understanding this context can help manufacturers appreciate the why behind the requirements:
- Evolving EU Cyber Strategy: The EU has steadily been ramping up its cybersecurity framework. The original NIS Directive (adopted in 2016) was the first EU-wide law on cybersecurity for critical infrastructure, and NIS2 is a major upgrade reflecting lessons learned and the changing threat landscape. Meanwhile, the EU Cybersecurity Act of 2019 empowered ENISA and created voluntary certification schemes for certain products. The Cyber Resilience Act goes a step further by making product security mandatory, effectively integrating cybersecurity into the single market requirements for product safety.This mirrors what the EU did for privacy with GDPR – setting a high bar and enforcement regime that forces organisations worldwide to improve practices if they want to do business in Europe.
- Extension to New Sectors: Prior to NIS2, many manufacturing firms may not have been legally required to follow specific cyber rules (unless they were in sectors like chemicals or healthcare devices, which had their own regulations). Now, NIS2 explicitly brings much of the manufacturing and industrial sector into scope as “important” infrastructure. This reflects the reality that manufacturing is part of the critical supply chain – if a major automotive or semiconductor plant is hacked and stops production, it can have national and even global ripple effects. The law firm Shoosmiths points out that cyber incidents in core manufacturing (like those in metals and semiconductor industries) have had far-reaching impacts, reinforcing why regulators see manufacturing as vital to protect. In short, the regulatory environment is catching up to the interdependencies of modern industry.
- Focus on Lifecycle and Resilience: Both CRA and NIS2 emphasize lifecycle security and continuous improvement, rather than one-time compliance. The CRA’s requirement for ongoing product support and vulnerability management aims to tackle the problem of products becoming insecure over time if left unpatched. NIS2’s ongoing risk management and reporting duties push organisations to continually assess and upgrade their security as threats evolve. This dynamic approach builds on frameworks like NIST and ISO 27001 which use the concept of continuous improvement (Plan-Do-Check-Act) for security management. It also aligns with emerging global trends – for instance, the U.S. government has been pressing for software vendors to provide SBOMs and ensure post-market vulnerability handling, which is very much in the spirit of the CRA.
- Integration with Other Laws and Standards: Complying with CRA and NIS2 will often dovetail with meeting other legal obligations. For example, GDPR (the EU data protection regulation) requires appropriate security of personal data – NIS2’s measures (like access control, encryption) will help with that where personal data is involved in manufacturing processes. If you manufacture medical devices or automotive systems, there are existing sector-specific cybersecurity guidelines which the CRA does not replace but rather complements by ensuring baseline security in any digital components of those devices. Manufacturers should be prepared for a more harmonised regime: the CRA will leverage harmonised European standards (developed via CEN/CENELEC) to define the technical specifics. This means standards like those in the IEC 62443 series or the ISO 21434 (for automotive cybersecurity) could become formal “state of the art” benchmarks. Companies already following such standards will find themselves ahead in compliance.
- Higher Accountability: The new directives also raise the bar on accountability. Notably, NIS2 includes provisions to hold senior management accountable for non-compliance (including potential temporary bans from management positions in severe cases). This echoes the approach taken in financial regulations and shows cybersecurity is now a board-level responsibility. We can expect regulators to scrutinise not just technical controls but also whether companies have appropriate governance – for example, do they conduct board-level cyber risk reporting? Do they allocate sufficient resources to security? Manufacturers will need to document their efforts thoroughly (indeed, documentation is a theme – CRA requires extensive product security documentation, and NIS2 will likely require evidence of risk assessments, policies, training, etc., during audits).
Conclusion: Turning Compliance into Opportunity
Navigating the EU’s Cyber Resilience Act and NIS2 Directive may feel challenging, but it ultimately boils down to implementing sound cybersecurity practices that will benefit manufacturers in the long run. By securing the products you make and the systems you operate, you are not only meeting legal requirements but also protecting your business from costly disruptions, safety incidents, and reputational damage.
Manufacturers using industrial software should engage with their technology providers and partners now to ensure everyone is on the same page regarding these new obligations. If you use Rockwell Automation’s systems, for instance, reach out to discuss how they are enhancing product security to meet the CRA (so that by 2027 your equipment comes pre-compliant) and how they can support your NIS2 compliance efforts through improved OT security services. Similarly, communicate with all critical suppliers about cybersecurity – compliance is a shared journey.
While regulatory texts can be dry, the essence of CRA and NIS2 is practical: build secure products, secure your operations, know your risks, and be ready to respond. Consider compliance projects as an opportunity to modernise legacy systems, to invest in staff skills, and to differentiate your business. Companies that can demonstrate strong cyber resilience will not only avoid fines, they’ll gain trust with customers and partners who are increasingly concerned about security.
In summary, to comply with the CRA and NIS2, manufacturers should embed cybersecurity into every phase – from product design and supply chain selection to daily operations and incident response. With the right approach, meeting these EU requirements can go hand-in-hand with driving innovation and reliability in the manufacturing sector. By acting now and treating cyber resilience as a core business goal, manufacturers can turn what might seem like regulatory burdens into a competitive advantage in our digital, connected era.
Compliance is not just a box-ticking exercise – it’s a catalyst for stronger security and sustained success in the evolving industrial landscape.
References:
- Rockwell Automation – “What’s new in NIS2” (NIS2 Directive overview and requirements for essential/important entities)rockwellautomation.com.
- Hyperproof – Understanding the Relationship Between NIS2 and the EU Cyber Resilience Act (Key focus areas of NIS2 vs CRA, timeline, and compliance insights)hyperproof.io.
- Industrial Cyber – What the Cyber Resilience Act requires from manufacturers (Explanation of CRA scope, CE marking for cybersecurity, and documentation requirements)industrialcyber.co.
- TXOne Networks – The Cyber Resilience Act: A Guide for Manufacturers (Summary of CRA obligations: technical documentation with SBOM, 5-year support, incident reporting within 24h)txone.com.
- Shoosmiths LLP – NIS2: What Manufacturers and Distributors need to know (Legal perspective on NIS2 scope for manufacturing, incident reporting 24h, and CRA product security requirements)shoosmiths.com.
- Rockwell Automation Blog – Achieve NIS2 compliance using existing frameworks (Advice on using frameworks like ISO 27001/IEC 62443 to meet NIS2, and link to future CRA compliance)rockwellautomation.com.
- European Commission – Shaping Europe’s Digital Future: Cyber Resilience Act (EU announcement highlighting secure-by-design and lifecycle security for products)hyperproof.io.
- Hyperproof – Supply chain security under NIS2 and CRA (Both regulations require strengthening vendor security and sharing information to manage supply chain cyber risks)hyperproof.io.

